Commvault Announced Acquisition of Clumio
AWS Shared Responsibility Model: What You Need to Know

Picture this: you’ve just purchased a state-of-the-art, impenetrable safe to store your most valuable possessions. You’re confident in the security of this safe, but there’s one catch – the lock and key are shared between you and the manufacturer. In this scenario, how secure is your safe? This analogy represents the unique challenge presented by the AWS Shared Responsibility Model, where cloud security is distributed between Amazon Web Services (AWS) and its users. But what exactly does this mean for you and your data? As a customer of AWS, understanding your role in this model is crucial, as it can be a determining factor in how effectively your organization optimizes its cloud security. In this blog post, we will unravel the mysteries of the AWS Shared Responsibility Model and provide the vital information you need to safeguard your valuable digital possessions on the cloud.
AWS’s Shared Responsibility Model outlines the division of responsibilities between AWS and its customers when it comes to security and compliance in the cloud. AWS manages the security of the cloud, meaning everything from the infrastructure to the physical facilities, while customers are responsible for securing their own data in the cloud and taking appropriate measures to meet specific compliance requirements. This model allows for a flexible approach to security that can be tailored to each customer’s unique needs.
Understanding the AWS Shared Responsibility Model
The AWS Shared Responsibility Model is a framework that outlines how security and compliance responsibilities are shared between AWS and its customers. It is important for businesses to understand this model, as it determines which security controls they are responsible for implementing and which ones are managed by AWS.
Under this model, AWS is responsible for security of the cloud, while customers are responsible for security in the cloud. This means that AWS is responsible for the underlying infrastructure, such as data centers and networks, as well as managing access control to those resources. On the other hand, customers are responsible for securing their own applications and data within their AWS environment.
For example, consider a business that uses Amazon EC2 instances to host their web application. AWS is responsible for ensuring that the physical servers on which these instances run are secure, but the business is responsible for configuring firewalls and security groups to protect their own data.
It is important to note that responsibilities can be shared depending on the specific services used by each customer. The AWS Shared Responsibility Model provides guidelines on which responsibilities should be considered when deploying solutions within an AWS environment.
To further illustrate this point, consider a business that uses both Amazon S3 and Amazon EC2. While AWS manages the physical infrastructure for both services, the responsibility for securing data stored in S3 is mainly on the customer, whereas protecting data on EC2 instances falls under their responsibility.
Some critics argue that there is still confusion around what security risks are being shared. It is important for businesses to take ownership of their end of cloud security risk management so as not to rely solely on providers such as AWS. However, following best practices provided by vendors can go a long way in reducing risk factors in any partnership.
- The AWS Shared Responsibility Model outlines how security and compliance responsibilities are shared between AWS and its customers, with AWS being responsible for the security of their physical infrastructure, and customers being responsible for securing their own applications and data within an AWS environment. It is important for businesses to understand this model to determine which security controls they should implement. However, businesses should also take ownership of their end of cloud security risk management and not solely rely on providers like AWS, while following best practices provided by vendors can lower risk factors.
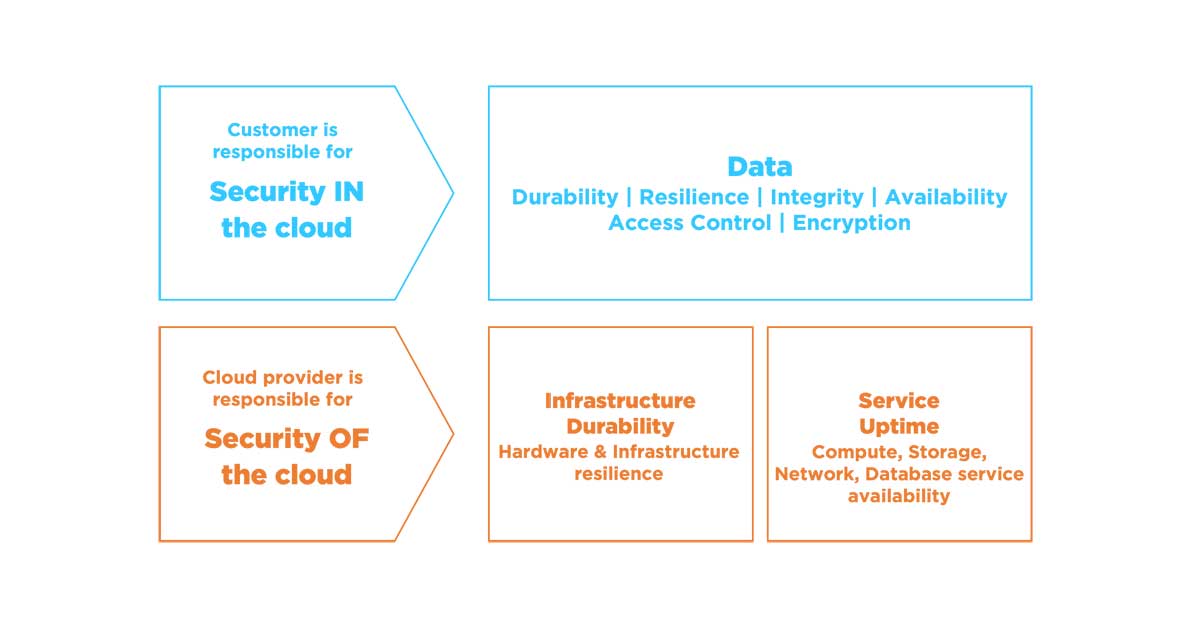
Security of the Cloud vs. Security in the Cloud
One of the key concepts that cloud users must understand is the difference between security of the cloud and security in the cloud. As previously stated, AWS is responsible for managing and securing the underlying infrastructure of their cloud service. This is referred to as security of the cloud, as it involves securing the physical infrastructure.
Security in the cloud refers to data protection within a customer’s applications and servers hosted in the cloud. This responsibility falls on customers rather than AWS. It includes managing user access control, network settings and configurations, as well as encryption of sensitive data.
Think of security of the cloud as a hotel’s safe deposit boxes where physical things one keeps are stored. In contrast, security in the cloud is similar to passwords needed to protect one’s one belongings from intruders while inside their hotel room.
It is important to note that businesses should not ignore their responsibilities under security in the cloud just because AWS is responsible for security of the cloud. With this shared responsibility model, AWS provides best practices and guidelines on how customers can ensure their own security in addition to what AWS already provides.
For example, Amazon EC2 instances protected by a firewall provided by AWS have strict default settings with an option to customize. The customer must configure these firewalls on their end such that they will be able to control who can access their instance environments on top of what AWS has done.
Critics argue that relying solely on best practice documentation can result in inadequate protection against attacks. Cloud users need to be diligent about configuring their own systems according to current standards and proactive measures like automated patching systems that alert system managers on when patches become available.
Implementing the AWS Shared Responsibility Model
The AWS Shared Responsibility Model requires both the customer and AWS to take part in ensuring the security and compliance of their system. AWS manages and controls the physical infrastructure stack, while customers are responsible for securing their applications as well as handling identity access management (IAM). It is therefore crucial that customers implement the model effectively to mitigate any potential threats and maintain security.
One key aspect of implementing the model is identifying and evaluating your organization’s data processing needs. This includes understanding your data, classifying each data type and assigning responsibilities to ensure the secure processing and storage of all data. Any sensitive or regulated data must be stored in controlled environments, with strict access control measures in place.
Another important step is selecting a secure architecture design that incorporates access control, network segmentation, logging, monitoring, encryption services, and vulnerability management practices. Access should only be granted based on individual user roles and responsibilities through IAM best practices. At every stage of implementation, cybersecurity awareness training program must be instituted for all employees to ensure they understand their role in maintaining high levels of security.
For instance, let’s say you’re building an application on AWS using Amazon EC2 instances. As per the shared responsibility model of AWS, while AWS takes care of physical security and availability of hardware resources underlying Amazon EC2 instances as well as networks associated with them; it’s your responsibility to manage guest operating systems (including updates) and firewall configurations applied within these machines.
To further solidify this point about user access control, you can use AWS Identity and Access Management (IAM) tools to grant permissions based on what each user needs to do – for instance only allowing read permissions for logs or database queries. IAM also allows for integration with other services such as databases so that users don’t need remote connections – instead they can connect directly within your private network which minimizes exposure points.
An interesting debate that comes up is whether it’s better to be proactive or reactive when it comes to security. The former argues for planning ahead and anticipating potential threats, while the latter involves arriving at solutions after a security breach has already occurred. As with most debates, there are pros and cons to both approaches; however in terms of implementing the AWS Shared Responsibility Model, being proactive is definitely the way to go. This includes conducting periodic vulnerability scans and penetration tests, reviewing logs regularly to identify anomalous activity, and keeping an up-to-date disaster recovery plan ready in case of emergencies.
- According to a 2020 IDC survey, 64% of IT professionals are leveraging security as a shared responsibility under cloud service providers like AWS to maintain a secure cloud environment.
- In a 2019 McAfee report, it was found that organizations using AWS experienced more than 2,700 security threats in a month on average, emphasizing the importance of adhering to the shared responsibility model for enhanced protection.
- A 2018 Gartner report estimates that by 2025, 99% of cloud security failures will be the customer’s fault, highlighting the importance of understanding and managing customer responsibilities within the shared responsibility model.
User Access Control and Data Management Practices
One area where customers have considerable responsibility under the shared model is that of user access control and data management practices. When dealing with critical data, customer permissions must be audited regularly as part of your IAM best practices. In doing so you can ensure that each user only has access to what they need and nothing more.
Data management best practices require you to enforce strict controls over how data is stored, processed, transmitted, accessed and deleted throughout its lifecycle. Data sensitive environments should be secured by role based access control mechanisms as well as encryption solutions like transport layer security (TLS) which safeguard against eavesdropping and man-in-the-middle attacks.
Suppose you have a team of developers working on critical applications in your infrastructure. By using AWS IAM policies in conjunction with Amazon CloudWatch Logs Insights, you can track user activity to find out who accessed what parts of your system and when. With this data, you can determine whether there are any unusual patterns or errors in their login attempts which could indicate a potential security breach.
Additionally by integrating various AWS services you can create a secure environment where users are prevented from leaking sensitive information outside your organization. An example would be using Amazon Macie along with AWS KMS to manage encryption keys so that valuable data stored on S3 is automatically encrypted when it’s written and decrypted when it’s read. This way, unauthorized access to sensitive information is prevented even if your buckets are accidentally exposed.
When it comes to managing user access controls there’s no one-size-fits-all approach; instead different organizations have different requirements and hence must implement a solution that works best for their use case. However, in order to efficiently implement the AWS Shared Responsibility Model genuine effort needs to be made by customers to maintain an environment which is secure and compliant with industry standards.
Advantages of the AWS Shared Responsibility Model
The AWS Shared Responsibility Model has numerous advantages for companies seeking to secure their IT infrastructure while maintaining flexibility in deployment. One clear advantage is that the model allows organizations to focus on their core competencies, rather than expending time and resources on IT security. By entrusting AWS with responsibility for “Security of the Cloud,” organizations can instead concentrate on managing their data, applications and other critical business functions.
Another advantage is that AWS manages all the physical and network infrastructure, reducing the risks of unauthorized access, data breaches or service disruptions. With its global network of data centers, AWS provides reliable, high-performance hosting services around the clock. This level of support enables businesses to scale up or down easily as required, without having to manage hardware upgrades or network implementations themselves.
Furthermore, both AWS and its customers share control over data management practices, meaning that customers can choose the best tools and technologies to manage their data in a way that aligns with their own compliance requirements. This also means that customers can leverage AWS’s industry-leading security controls and compliance certifications to demonstrate adherence to regulatory frameworks.
For example, a healthcare provider using an electronic health record system could use Amazon RDS to host its database while implementing encryption at rest to meet HIPAA compliance requirements. By leveraging AWS’s expertise in security and compliance controls, the company can avoid many of the challenges of managing its own IT infrastructure while still meeting key regulatory standards.
Another benefit is that companies can take advantage of the scalability and agility offered by cloud computing platforms like AWS. With the ability to provision resources on demand and scale up or down quickly as required, businesses can respond more readily to changing market conditions while avoiding unnecessary costs.
Overall, the shared responsibility model offers a flexible yet robust approach to IT security that is tailored to each organization’s unique needs. By leveraging AWS’s broad range of tools and technologies for security and compliance, companies can implement best practices for data management and application security while focusing on their core competencies.
Enhanced Security and Compliance Flexibility
Security and compliance are critical components of any IT infrastructure, especially for businesses that handle sensitive or regulated data. The AWS Shared Responsibility Model provides enhanced security and compliance flexibility by enabling organizations to utilize a range of tools and technologies to meet their unique requirements.
One key advantage is that AWS offers multiple layers of security controls that can be used in various combinations to meet specific needs. For instance, customers can use Amazon Inspector to assess the security vulnerabilities of their applications while leveraging features like AWS Identity and Access Management (IAM) to control user access.
Additionally, AWS provides enterprise-grade encryption capabilities that enable customers to secure their data both at rest and in transit. This includes support for Secure Sockets Layer (SSL)/Transport Layer Security (TLS) for web traffic, Key Management Service (KMS) for cryptographic key handling, and Hardware Security Modules (HSMs) for enhanced security. By making these technologies available, AWS enables customers to build highly secure architectures within its cloud environment.
Another way that the shared responsibility model supports enhanced security and compliance flexibility is by enabling organizations to maintain control over key aspects of their IT infrastructure. For example, using AWS services like Amazon EC2 Dedicated Hosts allows customers to host instances on hardware dedicated exclusively for their use, thus providing greater control over their computing environment and reducing the risks of unauthorized access or other security issues.
An organization handling classified information may require stricter controls than those provided by default shared tenancy architecture. In such cases, using a dedicated hosting solution through AWS would ensure a more secure computing environment without compromising flexibility or performance.
Finally, AWS offers a range of compliance certifications that can help organizations meet regulatory or industry-specific requirements. Compliance certifications applicable across different industries include ISO 27001, PCI DSS, SOC 1/2/3, and HIPAA, among others. By leveraging these certifications and other security tools in combination with the shared responsibility model, organizations can build secure and compliant IT infrastructures that meet their specific needs.
In the next section, we will explore some of the challenges that organizations may face when implementing the AWS Shared Responsibility Model.
Addressing Potential Challenges in the Shared Model
While the AWS Shared Responsibility Model provides a clear framework for dividing responsibilities between customers and service providers, some challenges can arise. These challenges can include understanding who has responsibility for particular elements of security, managing user access controls, and ensuring that compliance regulations are met. In this section, we’ll explore some common challenges faced by organizations when implementing the Shared Responsibility Model and offer suggestions for addressing them.
One common challenge that organizations face is determining what they are responsible for versus what AWS is responsible for in terms of compliance. Depending on the AWS services used and the IT environment integration, different areas of responsibility may fall on different parties. For example, an organization may be unclear about which regulations are applicable to its use of AWS services or how to configure them properly. A helpful approach here would be to consult AWS documentation or experts in the field to clarify any areas of uncertainty.
Another potential challenge is ensuring that users have appropriate access controls while still maintaining proper security posture. The Shared Responsibility Model requires that customers manage their own identities and access control policies within their own environment using IAM tools provided by AWS. This means that customers must ensure that users are authorized to access only what they need to perform their duties. Additionally, customers must ensure that roles and permissions are assigned appropriately based on job function, seniority level, etc., while also limiting access when not needed. Failing to adequately address these concerns can lead to severe consequences such as lost data or compromised systems.
To address these issues, some organizations choose to implement separate identity management solutions outside of AWS. While this can simplify administration and provide greater control over user access policies, it also introduces additional complexity into already complex environments. Moreover, many third-party vendors lack mature integrations with AWS services or may require custom development efforts.
One potential solution is for organizations to utilize AWS’ Identity and Access Management (IAM) service. IAM offers a range of tools and services that enable organizations to define, manage, and enforce policies for access control across their AWS environment. Additionally, customers can leverage IAM roles to provide temporary credentials to external users or use federated login options to support single sign-on (SSO) capabilities.
Another challenge that may arise within the Shared Responsibility Model is ensuring that sufficient levels of security are maintained at all times. While AWS manages the security of its infrastructure layer and abstracted platform services, customers are responsible for implementing secure guest operating systems, applications, and data configurations. One helpful analogy here is thinking about building a house: Just as contractors must ensure that the foundation is stable before adding additional construction layers, organizations must implement appropriate baseline security protocols before entrusting more data or workloads to AWS.
In conclusion, while the AWS Shared Responsibility Model provides an excellent framework for dividing up responsibilities between providers and customers, challenges can arise when implementing it in practice. These challenges commonly include issues around compliance regulations, user access controls, and implementation of appropriate security policies. By leveraging existing AWS tools like Identity and Access Management (IAM), carefully defining areas of responsibility, and following best practices around security configuration management, organizations can better address these challenges and realize the benefits of this model over time.
Common Questions
What are the customer’s responsibilities in the AWS shared responsibility model?
In the AWS shared responsibility model, customers are responsible for securing their own data and applications up to the operating system. This includes configuring security settings, managing access controls, and conducting regular security assessments.
According to research conducted by Gartner, “through 2025, 99% of cloud security failures will be the customer’s fault” (Gartner, 2018). This highlights the importance of understanding and fulfilling customer responsibilities in the shared responsibility model.
AWS provides a variety of tools and resources to help customers meet their responsibilities. These include security features such as Identity and Access Management (IAM) and Services like AWS Config which enables continuous monitoring and compliance checks.
Ultimately, it is crucial for customers to understand and take ownership of their responsibilities in order to safeguard their data and applications on the AWS platform.
What are the AWS provider’s responsibilities in the shared responsibility model?
In the AWS Shared Responsibility Model, the provider’s responsibilities include the security and management of the underlying infrastructure that supports the cloud. This includes physical security of data centers, network and firewall configuration, and operational security such as monitoring and incident response.
According to a report by Gartner in 2022, “AWS continues to be recognized as a leader in public cloud IaaS due to its comprehensive service offerings and expertise in running infrastructure at scale.” The report also highlights AWS’ strong position in security and compliance.
Additionally, AWS offers numerous security features for customers including identity and access management, encryption options, network security tools, and compliance certifications. These features are designed to help customers meet their own shared responsibility obligations.
However, it’s important to note that while AWS provides a secure infrastructure, customers are still responsible for securing their applications, data, and other assets within the cloud. This includes configuring access controls appropriately, patching operating systems and applications, and monitoring for potential threats or vulnerabilities.
Overall, understanding the shared responsibility model is crucial for any organization using cloud services. By working together with their provider (in this case AWS), customers can ensure their data and assets are properly secured in the cloud.
How does the AWS shared responsibility model differ from other cloud service provider models?
The AWS shared responsibility model sets itself apart from other cloud service providers by clearly defining the security responsibilities of both the customer and AWS. This means that customers have more control over their data and infrastructure while still benefiting from the security measures provided by AWS.
Unlike other cloud service providers, AWS takes responsibility for the physical security of their data centers, as well as the security of their cloud infrastructure. This includes the security of hardware, virtualization layer, storage location, and network infrastructure.
On the other hand, customers are responsible for securing their applications and data within the AWS platform. This includes configuring access controls, managing user identities and permissions, encrypting data in transit and at rest, and ensuring compliance with regulations.
According to a report published by Gartner in 2020, the AWS shared responsibility model played a significant role in helping customers improve their overall security posture. In fact, Gartner stated that “by 2023, 99% of cloud security failures will be the customer’s fault.”
In summary, by clearly outlining the security responsibilities of both parties involved, the AWS shared responsibility model provides customers with greater control over their own security while still benefiting from world-class cloud infrastructure security provided by AWS.
Are there any common misconceptions about the AWS shared responsibility model?
Yes, there are common misconceptions about the AWS shared responsibility model. One of the most widespread is that customers tend to believe that once they move to the cloud, all security responsibilities shift entirely to AWS. However, this is not true, and it is important for businesses to understand how the responsibility is shared when using AWS.
According to a survey conducted by LogicMonitor in 2019, 66% of IT professionals believed that cloud providers were solely responsible for securing their customer data. Furthermore, 70% of those surveyed thought they were less accountable for security in a cloud environment compared to traditional on-premise IT infrastructures. These statistics suggest that there is still a misunderstanding regarding security and responsibility in the cloud.
It’s essential to note that while AWS manages physical security and compliance of its infrastructure, customers are responsible for managing security controls within their own accounts. Customers must ensure proper configuration of their applications and infrastructure and implement safeguards such as firewalls, identity access management (IAM), data encryption, patch management, and more.
To quote a statement from AWS’ Shared Responsibility Model whitepaper:
“Customers retain control of what security they choose to implement to protect their content, platform, applications, systems, and networks, no differently than they would in an on-site data center.”
In conclusion, understanding the AWS shared responsibility model is crucial for businesses who use AWS or plan to migrate to the cloud. It’s essential to recognize that although AWS does provide excellent security measures, customers must take responsibility for security controls in their own infrastructures.
How does the shared responsibility model impact security and compliance in AWS?
The shared responsibility model is a key concept in AWS that dictates the different security responsibilities between the cloud service provider and its customers. This model enables users to have greater control over their data, while also allowing AWS to maintain the necessary security standards.
From a security standpoint, customers are responsible for securing their applications, data and credentials, as well as managing compliance requirements, while AWS is responsible for the security of its infrastructure. Amazon claims that its infrastructure is designed to be highly secure, and that it has implemented extensive controls to maintain this level of security—such as physical and environmental controls, network and perimeter controls, and access controls. Additionally, AWS provides built-in security measures such as encryption, monitoring tools and identity and access management services.
In terms of compliance, AWS adheres to various industry standards such as HIPAA for healthcare organizations and PCI DSS for payment card processing companies. However, customers are ultimately responsible for ensuring they comply with any relevant regulations for their industry or region.
According to a report by McAfee in 2020, misconfigured cloud storage services were the primary cause of 1.5 billion records being exposed during the first half of the year alone. This highlights the importance of understanding one’s responsibilities in an AWS environment. Following best practices such as using multi-factor authentication (MFA) for user access and keeping sensitive data encrypted can greatly reduce the risk of data breaches.
Ultimately, understanding the shared responsibility model is crucial for proper security and compliance in AWS. By leveraging AWS’ infrastructure capabilities while also implementing effective security practices on one’s own end, businesses can ensure a secure cloud environment.

