Commvault Announced Acquisition of Clumio
Air Gap Backup: Why it Matters for Data Protection
Over the past few years, we have seen that traditional data protection methods needed to evolve in order for organizations to better protect themselves from potential threats, both internal and external. We also see that as customers continue to embrace cloud-first and cloud-native strategies, they need to ensure that their data protection strategies can evolve as quickly as their workloads. In this guest blog post, I’ll discuss some of these challenges, and how Clumio helps customers overcome these challenges.
Why is air-gapping important?
Customers are continuing to see an evolution in the number and types of threats that they face. No longer is the concern of accidental file deletion or loss of a primary site enough for an organization to worry about – these days, customers need to be sure that they are protecting against a variety of threats and ensure that their data is protected, even during scenarios that aren’t top of mind. Let’s look at a few in further detail:
- Ransomware – This is quickly becoming a top concern with customers, given that organizations of all sizes are falling victim to ransomware attacks, some of which end up making headlines for all of the wrong reasons. When a ransomware attack such as WannaCry is successful, it will generally encrypt all files on a user’s workstation or server, requesting that a payment be made in Bitcoin to the attacker to decrypt the files. Should the ransomware attack spread to critical infrastructure, it can be an all-hands effort to try and remediate, taking down business operations for long periods of time. Recently, the US Cybersecurity and Infrastructure Agency released an advisory, co-authored by the FBI and Department of Health & Human Services, warning of an “increased and imminent cybercrime threat to U.S. Hospitals and Healthcare providers.” New ransomware variants are seen regularly, and it is unreasonable for customers to consider a single-pronged strategy to defend against a single ransomware variant or even groups of variants.
- Bad Actors – There are scenarios where bad actors – both internal and external to an organization – can present a threat. External bad actors may be able to gain unauthorized access to critical systems in a number of ways, such as user credentials being accidentally exposed in public code repositories, or user credentials being stolen via malware or phishing attacks. Internal bad actors (AKA Insider Threats) are less common than external bad actors, but do happen – especially if there is an employee or contractor that has the right levels of system access along with malicious intent to use that access in a way that would cause intentional harm to an organization by deleting systems and backups.
- Accidental Snapshot Deletion – Accidents can and do happen. It can be a situation that seems innocuous enough, where an engineer with good intentions removes snapshots in order to save on costs without fully realizing the business impact of deleting these snapshots. These accidental incidents are still a threat, and organizations need to look at ways to help them recover from these accidental scenarios in a quick and effective manner.
How you can secure your data with Clumio's air gap backups
One of the larger benefits to the Clumio service is that it provides customers with an air gapped and immutable data protection solution for storing backup data. Let’s take a deeper look into how Clumio is able to achieve this.
To achieve the air gap for data protection, Clumio stores all data on Amazon S3 located in a separate Clumio-owned AWS account. A customer does not have direct access to any resources residing in the Clumio service. Role-Based Access Control is only possible via the Clumio service UI (or Clumio REST APIs) which limit the operations that a customer can perform by design. Second, when backing up data, Clumio never overwrites existing data on Amazon S3, it will only append. This ensures complete data integrity for the restore points that are defined as part of a Clumio Backup Policy.
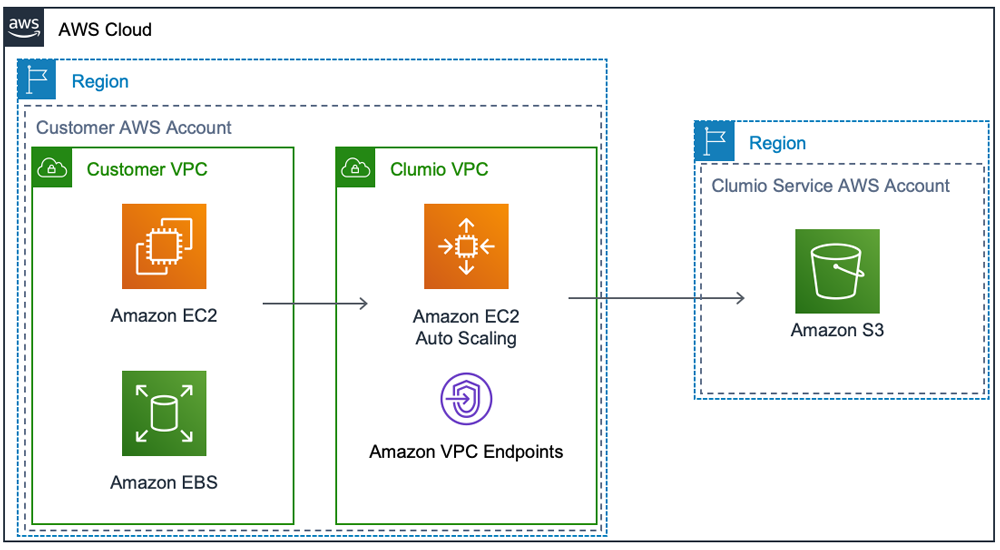
These approaches help customers solve for a number of potential areas of concern that have been previously mentioned in this post, specifically :
Ransomware – There are ransomware variants such as Ryuk that look to encrypt backups as part of an attack pattern. With Clumio, having your backups stored in an immutable format in a separate account which you don’t have access to ensures a solid layer of protection against such an attack. If a ransomware attack were to occur, customers can simply choose a restore point prior to the ransomware incident, and recover from that point. Clumio also provides customers the ability to restore to a different AWS account of your choosing (if needed), which can be beneficial for IT Security teams to perform a full forensic analysis on the impacted AWS account, while not impacting business operations once the restore to a new AWS account has completed.
Bad Actor – For situations where account credentials are compromised and critical resources are modified or deleted, Clumio’ s air gapped protection ensures that a bad actor (no matter if internal or external) cannot delete the backups that exist in the Clumio service. This is a better approach than simple Amazon EBS and Amazon RDS snapshot storage in the same AWS account, since a bad-actor can also choose to delete historical snapshots with no recourse available to the customer once the snapshots have been deleted. This also provides a layer of protection beyond cross-account snapshot copies when the second account is owned by the customer, since destination AWS account may not always be properly secured, or cross-account roles with sufficient privileges could exist between both accounts that would allow for deletion of cross account snapshot copies to occur.
Accidental Snapshot Deletion – When using Clumio, it is impossible for a customer to delete restore points -even accidentally – within the Clumio service. Should a customer accidentally delete an Amazon EBS or Amazon RDS snapshot and the resource is protected by the Clumio service, this does not impact the functionality of the Clumio service, and you would still be able to recover from previous Clumio restore points. Scheduled Clumio backups will still continue to function normally as well, causing no disruption in operations
Summary
We’ve seen how there are multiple threats that customers need to account for when defining a data protection strategy for their organization, although we just scratched the surface by naming some specific threats.
