Commvault Announced Acquisition of Clumio
Compliance in the Cloud
“If you have built castles in the air, your work need not be lost; that is where they should be. Now put the foundations under them.”
— Henry David Thoreau, Walden
Enterprises require the most robust security available and Clumio has made security the primary guiding principle of how we build our service. We made it our goal to achieve ISO/IEC 27001:2013 (more commonly known as “ISO 27001”) certification and to perform an SSAE 18 audit for a SOC 2 report within the first 12 months of our emergence into the market. Robust information security policies, procedures, and controls are foundational to Clumio’s “Always-On Security” approach. From the beginning, we built security into everything we did, and information security doesn’t begin or end with encryption. Using Clumio for backup, you’re getting best of breed encryption and security controls audited to the highest standards. We take data protection seriously in our platform and our people throughout the entire organization. I’d like to share some of the learnings from the journey we took to build our security fortress.
Why?
I’ve heard people in the technology industry state that they “have to” achieve ISO 27001 certification because “it’s a business necessity”, or because “customers won’t trust us without it.” Perhaps, but statements like this aren’t the core reason to embark on an information security program. The “why” of choosing to implement ISO 27001 is to proactively assess, monitor, and minimize threats to your organization’s (and, if you’re a SaaS provider, your clients’) information security. Successful execution of the program’s policies and controls will indeed demonstrate credibility and engender trust with your clients when you complete an audit from a qualified assessor, but the purpose of the program is to have an organization-wide commitment to information security. Executive sponsorship of security efforts, security awareness at all levels, and continual improvement of the ISMS are critical internal benefits and should be the goals of any service organization. A successful ISO 27001 certification demonstrates that Clumio achieved an internationally recognized commitment to our own and our customers’ data security.
People and Processes
In a previous post, I spoke about encryption key management. It’s become commonly accepted that strong encryption is a necessary foundation for securing data whether the data is on your mobile phone or stored in the cloud. However, encryption is just a single brick in the information security fortress that all companies must build. An actual fortress has strong walls and a guarded gate; it also requires a garrison of trained soldiers and staff to ensure that it can operate well.
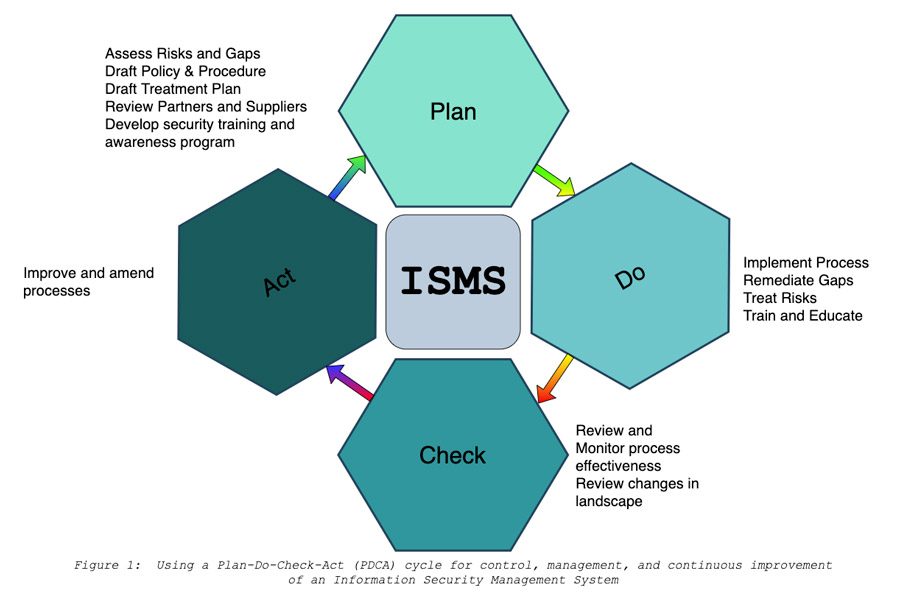
Standards, policies, and processes are necessary for any organization to operate efficiently. Many organizations that value information security adopt the standards prescribed by ISO 27001 as a blueprint for how their information security “fortress” will operate. ISO 27001 helps companies create, maintain, scale, and improve an Information Security Management System (ISMS). An ISMS provides a top-down, risk-assessment approach to managing threats and securing all data. While it provides standards that govern technologies, like the use of encryption, the guidance that addresses people and processes is equally valuable. Your employees are the fortress garrison, and their activities are critical to securing sensitive information. Enemies commonly attack an organization via its personnel: business email compromises, SMS phishing, infected USB device drops, etc. Education and training around information security awareness is paramount to ensuring a well trained, well informed garrison that’s equipped to identify and prevent the fortress defenses from breaches.
Protocols and Training
Clumio started on its ISMS implementation in March of 2019. We created policies and documented our operating procedures, aligning them with the policy objectives. You can think of this step as creating protocols for how to operate the fortress, e.g., how to raise or lower the gates, how to man the battlements, how supplies are delivered, etc. We then performed a risk assessment and developed a treatment plan. You can think of the risk assessment as a review of weaknesses in the fortress operations. Perhaps the change of guards leaves the gate unattended for 15 seconds, or the watchtowers had an obstructed view of a direction from which an enemy could approach. The treatment plan will mitigate or eliminate those risks. We might create a drill to change the guards at the gate with no time gap, or raise the watchtowers higher.
We then trained our employees on information security awareness, and emphasized to all the “why” for our processes and controls, along with the “how”. This critically important step is how personnel are informed of how to perform their duties whether routine or emergency, and why we perform them according to specified procedures (e.g., when a hostile force is attacking the fortress, #1 sound the alarm, #2 raise the drawbridge, and #3 man the battlements!).
3rd Party Supplier Management
No fortress could exist without external supplies and services. One of the often overlooked factors for organizations is the compliance posture of their suppliers and vendors. We evaluated all of our service partners and critical vendors for their own status. This is akin to making sure that the fortress supply lines are open, that the supply trains are guarded, that the supplies are high quality, and most importantly that they’ll arrive when the garrison needs them. If the required material is not available to the fortress personnel, the fortress ceases to operate.
We began monthly access reviews and quarterly ISMS management team meetings. The purpose of the reviews is to ensure that access procedures are being followed and to flag any anomalies or deviations from procedure. The guard at the gatehouse asks a potential visitor for their identification and the purpose of their visit; if it’s an authorized visit, it gets logged. If it isn’t, well… it still gets logged and the visitor is denied access. Reviewing those visitor logs keeps security tight. The management team meetings look at overall program effectiveness and take into account any changes in risk posture. Are there new risks introduced by a new vendor? Have previously low-grade risks become moderate or severe risks?
Change Control and Secure Software Development
We started running all of our changes to critical systems through a strict change management procedure. If we’re going to modify the procedure for changing the guard duty shift, or change the visitor procedure at the gatehouse, we must evaluate the plans, set measurable goals, review them, approve them, implement the changes, and most importantly measure the effectiveness of the new procedures. Widening a moat requires a construction plan, timelines, equipment, and a work crew. Did the widening procedure achieve the planned goal? This is where access reviews and quarterly meetings come in handy again.
We made numerous security-focused enhancements to our software development life cycle to align with the ISMS goals of continuous monitoring and improvement. We started with the specification and design stage; later stages of code development, review, testing, and promoting changes to release candidate status all received enhanced security procedures. I’ll discuss some of these subjects in detail in a future blog.
Continual Assessment and Improvement
Compliance is never a “one and done” task – the programs themselves are living entities that require routine tasks, management, measurement, analysis, and feedback to inform constant improvements. Annual surveillance audits are required, as well as full recertification at least every 3 years. Continual improvement of the ISMS must be demonstrated. Extensive software automation of tasks like network security scans, vulnerability scans, and log event monitoring are key to managing the size of the garrison needed; automated processes are more scalable and less error prone than manual ones. Cross-department communication and collaboration keep the garrison informed and effective. Executive and board sponsorship are crucial; the command staff set the tone and provide alignment to goals. For information security compliance to be effective, it must inform and influence the culture of an organization at all levels.
Please allow a final addition to the fortress metaphor. The title of this blog is “Compliance in the Cloud”, and Clumio was born in the cloud. We launched our platform on the premier cloud provider, Amazon Web Services. Think of this as picking an ideal location for your infosec fortress… a high hill with 360 degree visibility, a solid foundation, plenty of room for a moat, high walls, a strong gate, and a significant defensive perimeter. AWS itself is an ISO 27001 certified organization and provides physical and environmental controls required for Clumio’s platform operations. Effectively, they supply a lot of bricks, mortar, tools, and equipment for the fortress. The scope of our efforts can then be focused on our goals of delivering secure data protection to Clumio customers. We were able to tailor our fortress operations to these goals without unnecessary distractions. We’ll continue to build on these compliance programs in 2020 and beyond, with HITRUST CSF, FedRAMP, and more.
